Qualys Vulnerability
How Does a Vulnerability Management Program Protect Your Business?
The purpose of a vulnerability management program is to keep your network safe from known exploitations and ensure it stays compliant with any regulatory requirements.
It does this by analysing your network for any incompatibilities, missed updates and common weaknesses within the software you use.
It then prioritizes any vulnerabilities for remediation.
A vulnerability management program protects your business network from being breached through well-known vulnerabilities, making it much harder for cybercriminals to target your company. It can also help protect your business from any penalties associated with regulatory noncompliance, saving you money and your company’s reputation.
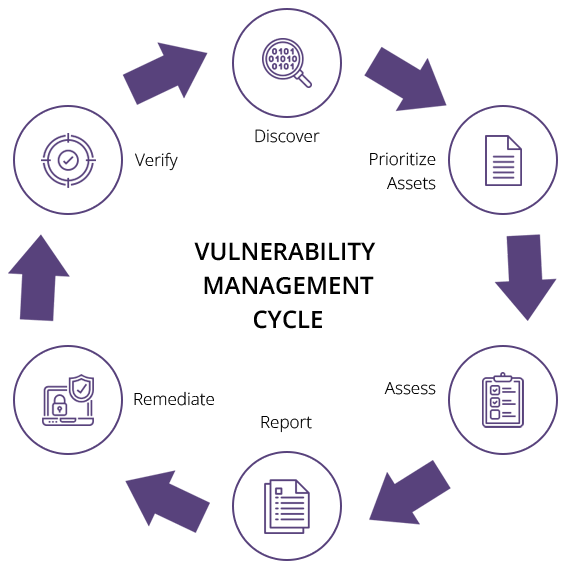
Vulnerability Management Life Cycle
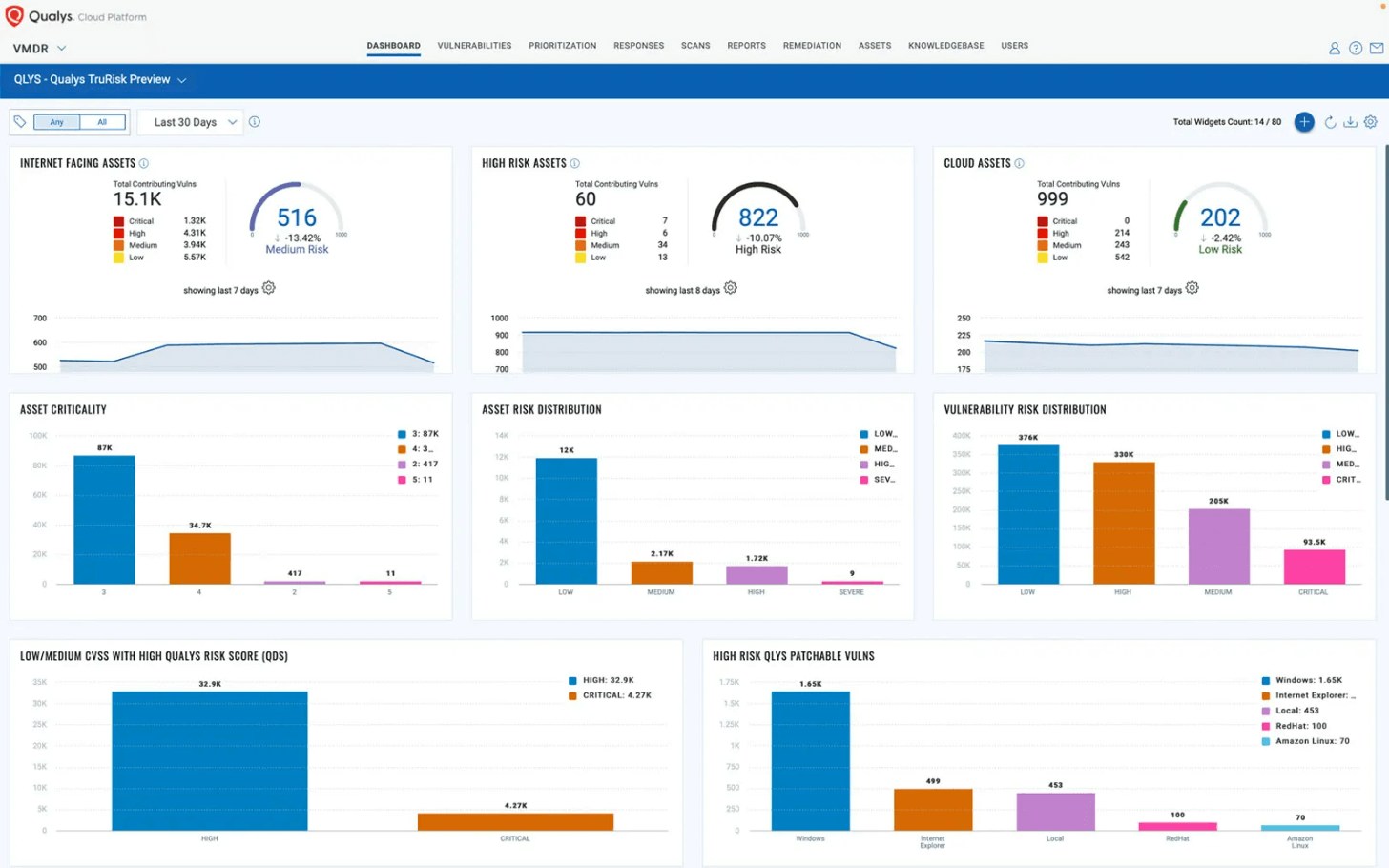
CyberGrape Vulnerability Management services are based on the Qualys Cloud Platform, combined with its powerful lightweight Cloud Agents, Virtual Scanners, and Network Analysis (passive scanning) capabilities bring together all four key elements of an effective vulnerability management program into a single app unified by powerful out-of-the-box orchestration workflows.
Qualys VMDR® enables organizations to automatically discover every asset in their environment, including unmanaged assets appearing on the network, inventory all hardware and software, and classify and tag critical assets.
Cybergrape's Vulnerability Management Programme
1. Pinging all network-accessible systems
2. Identifying services and open ports on relevant systems
3. Collecting detailed system information from systems that allow remote log-in
4. Comparing system information to a database of currently known vulnerabilities
This process builds the foundation for your vulnerability management process, ensuring all relevant systems are covered. It’s important to note that vulnerability scanners can sometimes be disruptive, whether from tying up significant bandwidth during the scan or causing some applications to behave erratically. To mitigate this, schedule the scan during times of slower traffic and either exclude problem applications or set the scans to be less disruptive. This is known as adaptive scanning.
1. Remediation: This is the preferred action to take whenever possible. Patching or fixing the vulnerability to prevent any chance of exploitation offers the most protection. Whether that involves software updates or blocking an application, the point of vulnerability remediation is to completely eliminate the threat.
2. Mitigation: If remediating a vulnerability isn’t feasible, mitigating it is the next best option. This is an option when your company can’t immediately remediate and needs to buy some time with the intention of remediating at a later date. The point of mitigation is to reduce the likelihood of the vulnerability being exploited, lowering the threat level temporarily until it can be fixed. Possible courses of action can include increasing authentication requirements or restricting access until a full solution is established.
3. Acceptance: Sometimes vulnerabilities will be identified that pose very low risk for exploitation or involve a remediation cost that far outweighs the cost of exploitation. In these cases, it may be appropriate to leave it alone and focus your attention on those that are more critical. Ideally, this should be kept to a minimum to keep potential security risks as low as possible.
Once this process is complete, it’s important to run an additional vulnerability scan to ensure the remediation actions were effective and have eliminated the most critical threats. If some have not been addressed as expected, it’s time to look further into the issue for alternative solutions.
1. Pinging all network-accessible systems
2. Identifying services and open ports on relevant systems
3. Collecting detailed system information from systems that allow remote log-in
4. Comparing system information to a database of currently known vulnerabilities
This process builds the foundation for your vulnerability management process, ensuring all relevant systems are covered. It’s important to note that vulnerability scanners can sometimes be disruptive, whether from tying up significant bandwidth during the scan or causing some applications to behave erratically. To mitigate this, schedule the scan during times of slower traffic and either exclude problem applications or set the scans to be less disruptive. This is known as adaptive scanning.
1. Remediation: This is the preferred action to take whenever possible. Patching or fixing the vulnerability to prevent any chance of exploitation offers the most protection. Whether that involves software updates or blocking an application, the point of vulnerability remediation is to completely eliminate the threat.
2. Mitigation: If remediating a vulnerability isn’t feasible, mitigating it is the next best option. This is an option when your company can’t immediately remediate and needs to buy some time with the intention of remediating at a later date. The point of mitigation is to reduce the likelihood of the vulnerability being exploited, lowering the threat level temporarily until it can be fixed. Possible courses of action can include increasing authentication requirements or restricting access until a full solution is established.
3. Acceptance: Sometimes vulnerabilities will be identified that pose very low risk for exploitation or involve a remediation cost that far outweighs the cost of exploitation. In these cases, it may be appropriate to leave it alone and focus your attention on those that are more critical. Ideally, this should be kept to a minimum to keep potential security risks as low as possible.
Once this process is complete, it’s important to run an additional vulnerability scan to ensure the remediation actions were effective and have eliminated the most critical threats. If some have not been addressed as expected, it’s time to look further into the issue for alternative solutions.